Beginning in software release 4.1 for the VSP 4000/8000, 4.2.1 for the VSP 7200, and release 4.0 for the VSP 9000, IS-IS accept policies for IPv4 is introduced. Prior to this release, the ISIS IPv4 routes received over the SPB cloud are installed directly into the routing table. There is no ability to filter those routes and apply incoming route policies to them. Hence, networks that are being migrated from other routing protocols to ISIS/SPB are vulnerable to routing loops. ISIS accept policy functionality provides a way to avoid such loops.
You can create an IS-IS accept policy for the Global Routing Table (GRT) or a Virtual Routing and Forwarding (VRF) instance. You can create an IS-IS accept policy on a switch that operates at a global default level or for a specific advertising BEB. You can also use the filter mechanism for ISIS accept policies to redistribute routes between different VRFs, or between a VRF and the GRT.
ISIS policies can also use either a service instance identifier (ISID) or an ISID list to filter incoming traffic. For inter-VRF route redistribution, an ISID value of 0 represents the GRT. For inter-VRF route redistribution between VRFs, the ISID is the source VRF (or remote VRF).
You can filter traffic with ISIS accept policies by:
- advertising BEB (nick-name)
- ISID or ISID list (ISID take precedence over an ISID list)
- route-map
You can use IS-IS accept policies to apply at a global default level for all advertising Backbone Edge Bridges (BEBs) or for a specific advertising BEB.
IS-IS accept policies also allow you to use either a service instance identifier (ISID) or an ISID list to filter routes. The switch uses ISIDs to define Virtual Services Networks (VSNs). ISIDs identify and transmit virtualized traffic in an encapsulated SPBM frame. IS-IS accept policies can use ISIDs or ISID lists to filter the incoming virtualized traffic.
IS-IS accept policies can also apply route policies to determine what incoming traffic to accept into the routing table. With route policies the device can determine which routes to accept into the routing table based on the criteria you configure, which can give precedence to advertised routes from a particular protocol, route-source, route-type, or through other criteria.

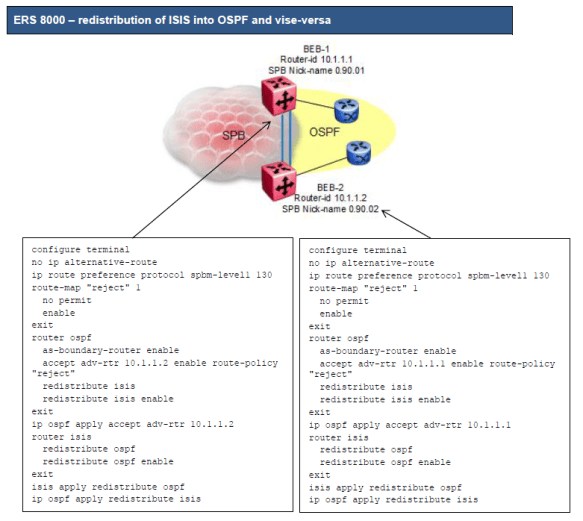
Note: The ERS 8800 does not support ISIS accept policies.
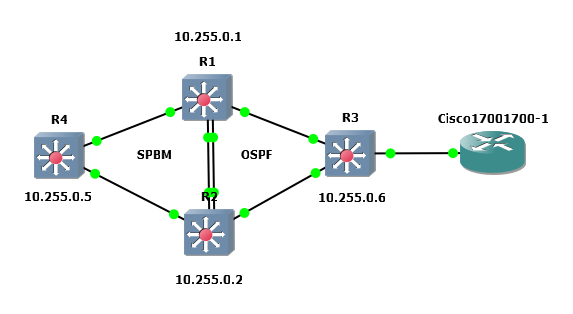
o There is no way to prevent one border router from accepting ISIS routes from the other border router
o The solution is to make OSPF preferred over ISIS by assigning ISIS a higher route preference over OSPF
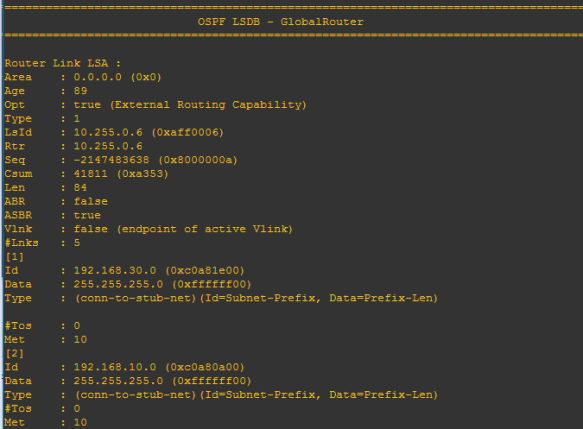
We can now use OSPF accept policies to prevent one border router from accepting OSPF external routes from another